Isolating Machines Within a LAN
Today, I decided to try creating a single point to point connection from a host on my LAN to the Pfsense box while at the same time, preventing it from connecting to other devices on the LAN. This is not like a VLAN where you’d have multiple networks on the same wires but I think it similar to how ISPs and some businesses engineer their networks.
I did it by creating a Virtual IP Alias on Pfsense to serve has the gateway with the subnet mask of /22 then assigning the second ip on the client with the virtual ip as the gateway and pointing the dns to that virtual ip as well.
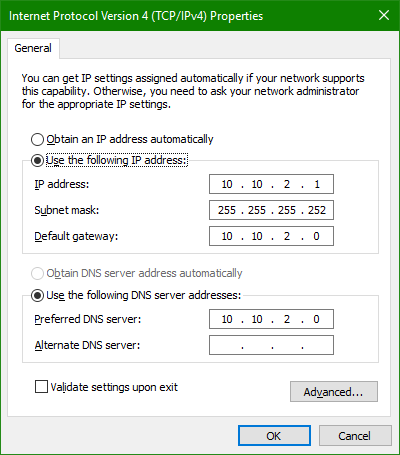
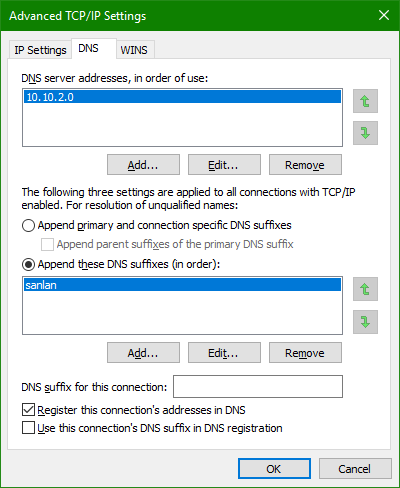
I then created aliases to point to the right things. Allow rules for the host to Pfsense and specific hosts on the larger lan. A general deny rule to prevent the isolated host from connecting to any private IP. Pretty basic stuff.
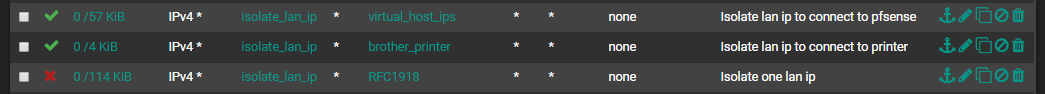
The goal is to isolate a thing while giving it access to the internet and approved nodes on the LAN. This is one method I’ve thought of outside of replacing all the switches on the network with managed ones for doing VLANS to different physical devices on the network. I don’t believe this is a fool proof method as all it’d take is some program or privileged person with the knowledge to modify the host’s IP settings and bump it back on the main LAN. It should work just fine for what I intend to use it for.
I’m curious to see what kind of security risks this poses to the main LAN should a isolated device become infected with something. Some research is required in the matter.
I think for the first real world test is to assign a computer to the isolated IP for my niece and nephew to use for school work. Maybe I can utilize OpenDNS for content filtering :) and of course, grant them unprivileged permissions on the computer. Microsoft has some parental tools for reporting child activity that could be useful.
That’ll be it for now. Until next time, keep geeking out!