DNS over TLS using PFsense
Before I begain, this guy talks a bit about it and does it the “old” way for systems with version 2.4.3 and older.
In version 2.4.4, pfsense was updated to offer support within the webui. Just 3 check boxes and your outgoing dns traffic is encrypted. You can do a packet capture on port 853 of you WAN interface to verify. I did a scan on my network and discovered there is still some plain DNS traffic but I’m unsure what to make of it. Some to microsoft and some to “akadns.org” (some sort of CDN for something). Maybe I need to do some checking at some point.
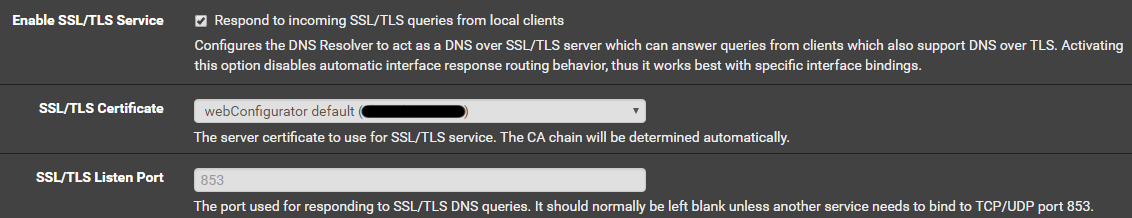
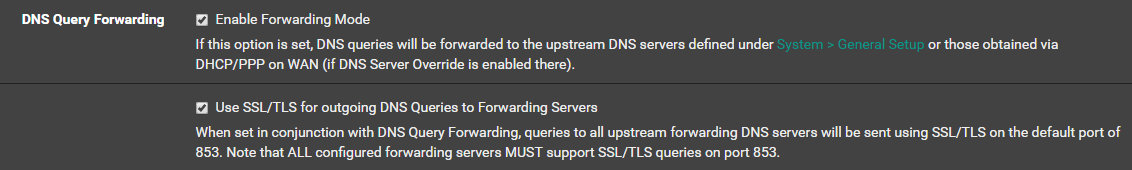
For those who run unbound on other systems (or older pfsense boxes), you can try this bit of config code to see if it will work for you.
forward-zone:
name: "."
forward-ssl-upstream: yes
forward-addr: 1.1.1.1@853
forward-addr: 1.0.0.1@853
forward-addr: 2606:4700:4700::1111@853
forward-addr: 2606:4700:4700::1001@853
Now to encrypt what little HTTP traffic I have without triggering Amazon and Netflix’s Anti-VPN/Tunneling block…
Enjoy!